
Categories: Capabilities
Cybersecurity Priorities: Aligning Defense Resources with Critical Missions

In the increasingly complex domain of national defense, effectively prioritizing cybersecurity resources is a critical yet challenging endeavor. With finite resources, the fundamental question facing the Department of Defense (DoD) becomes clear: What constitutes reasonable cybersecurity?
“It’s one thing to try to make something completely impervious to cyber assault, but you probably can't afford that.”
SPA Strategic Growth and Business Analyst, Mike Farren
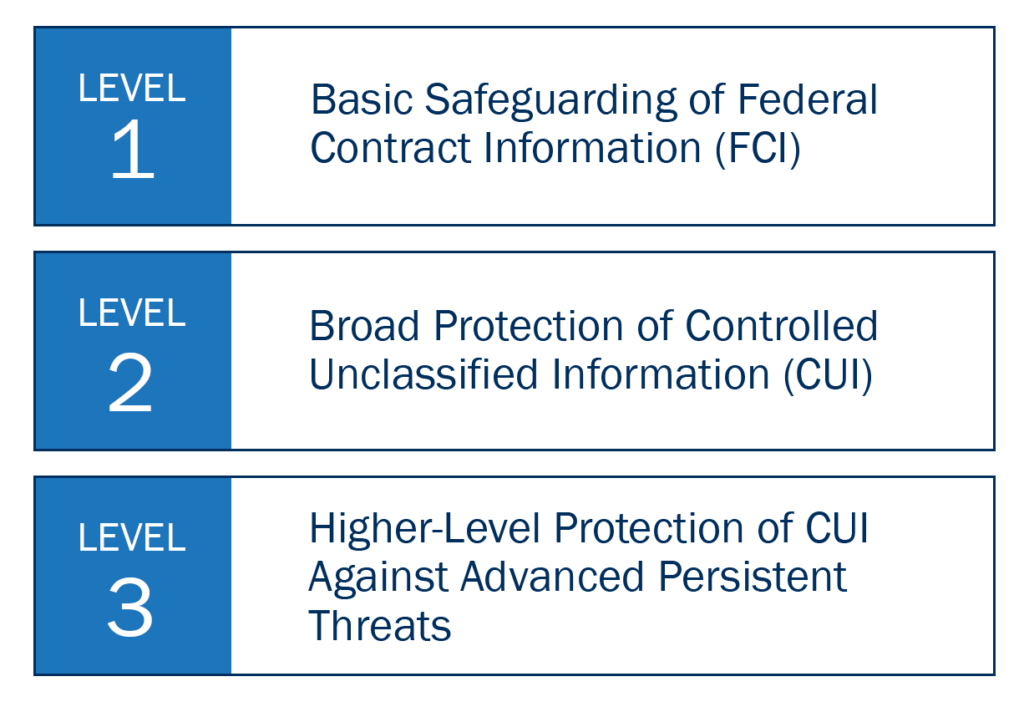
Farren highlights the DoD’s Cybersecurity Maturity Model Certification (CMMC) as an example of how the department seeks to establish tiered cybersecurity requirements based on the sensitivity of Controlled Unclassified Information (CUI). The model ranges from basic protective measures for simpler manufacturing roles (Level 1) to rigorous controls for firms engaged in advanced capabilities (Level 3).
However, Farren notes a critical gap: “It tends to be tied to the sensitivity of the CUI data as opposed to the criticality to the mission that data supports or enables. And I think that is still where DoD struggles in terms of where we apply the next cyber dollar.”
This issue extends beyond direct DoD assets into critical commercial infrastructure, such as power grids, telecommunications networks, and logistics operations—assets not always recognized as mission-critical but essential for operational success. A notable example is the 2017 NotPetya cyberattack, attributed to Russia. While the attack initially targeted Ukraine, it inadvertently affected global enterprises critical to U.S. interests, such as the shipping giant Maersk, which faced a shutdown costing more than $300 million. Pharmaceutical giant Merck, among many other firms, faced similarly significant operational disruption. These incidents underscore how vulnerabilities in commercial infrastructure can ripple through defense operations, significantly impacting readiness and mission success.
Cybersecurity compliance can place a disproportionate burden on smaller firms within the DIB, which often have only modest IT and cybersecurity budgets. Deloitte research shows:
- Small businesses typically spend only about 0.3% of revenue on cybersecurity.
- Firms generating under $10 million annually may afford only half a dedicated cybersecurity staff member.
- These constraints severely limit their ability to meet stringent DoD standards.
To help these smaller firms improve their cybersecurity approaches, the US government provides free or low-cost Cybersecurity-as-a-Service offerings, such as the Cybersecurity and Infrastructure Security Agency’s (CISA) Joint Cyber Defense Collaborative (JCDC), facilitating faster information sharing and coordinated responses to threats.
“Can DoD incentivize the adoption of better cybersecurity practices? Do we actually pay the firms? Do we provide tax incentives? Does DoD in some way bear the cost of their cybersecurity? Those decisions are still to play out,” Farren explains.
SPA would advise policymakers to explicitly align cybersecurity investments with clear, mission-critical objectives. This includes comprehensive interagency dialogues among the DoD, Department of Homeland Security (DHS), and other critical infrastructure stakeholders to address shared cybersecurity threats effectively.
Explore Further
This is the first of a four-part series on cybersecurity issues and challenges. Subscribe now to be informed when the rest of the series is published. Among other insights, you will get a deeper exploration of the “mission stack” framework and how it relates to broader cyber resilience in the upcoming post, “Strengthening National Cyber Resilience: Beyond Compliance to Mission Assurance.”
Related Posts
We invite you to subscribe and stay informed. Never miss an update as we continue providing the rigorous insights and expert analysis you rely upon to protect and advance our national security.




